HitmanPro.Alert Free Download
| System Requirements | |
| Supported Operating Systems | Windows XP*, Vista, 7, 8, 10 |
| Memory (RAM) | at least 512 MB |
| Hard Disk Space | ~ 5 MB |
| Processor | Intel Pentium 4 or higher |
| Supported languages | English (default), Deutsch (German), Español (Spanish), Français (French), Italiano (Italian), Nederlands (Dutch), Polski (Polish), Português Brasileiro (Portuguese Brazil), Pусский (Russian), Türkçe (Turkish), Dansk (Danish), Svenska (Swedish), 简体字 (Chinese Simplified), 繁體字 (Chinese Traditional), 한국어 (Korean), العربية (Arabic), Bahasa Indonesia (Indonesian). |
Product information
Install and run HitmanPro.Alert on your computer as preventive measure.
A software exploit is part of the malware collection. It takes advantage of ‘weak points’, or vulnerabilities, in commonly used software.
Until today you might think you are the one in charge of your computer and the software installed and active. Well, you should be in control. However, the scary part about these so-called exploits is, that they penetrate your system even without you being aware. These exploits unfortunately quite commonly also evade your respected Anti-Virus solution.
Once exploited, the code (attacker) can drop any malicious code on your system. Whether it is a Remote Access Trojan, a piece of Spyware, a worm or Ransomware, the end-effect is damaging.
We recognize that much malware is executed carelessly by the end-user himself, through the dropper (executable) itself or by allowing macro's within Microsoft Office.
But please note, that you can get infected by just surfing the internet with your just aged browser plugins.
What to do?
Of course, we do advise you to update and patch ALL your commonly used software regularly. This is surely a necessity, but remember that even the software providers do not know about prospective vulnerabilities in their own software products.
Thus, ideally we want a security solution preventing exploitation all together, without knowing the nifty details about all the diverse programs it protects. We find this protection in HitmanPro.Alert.
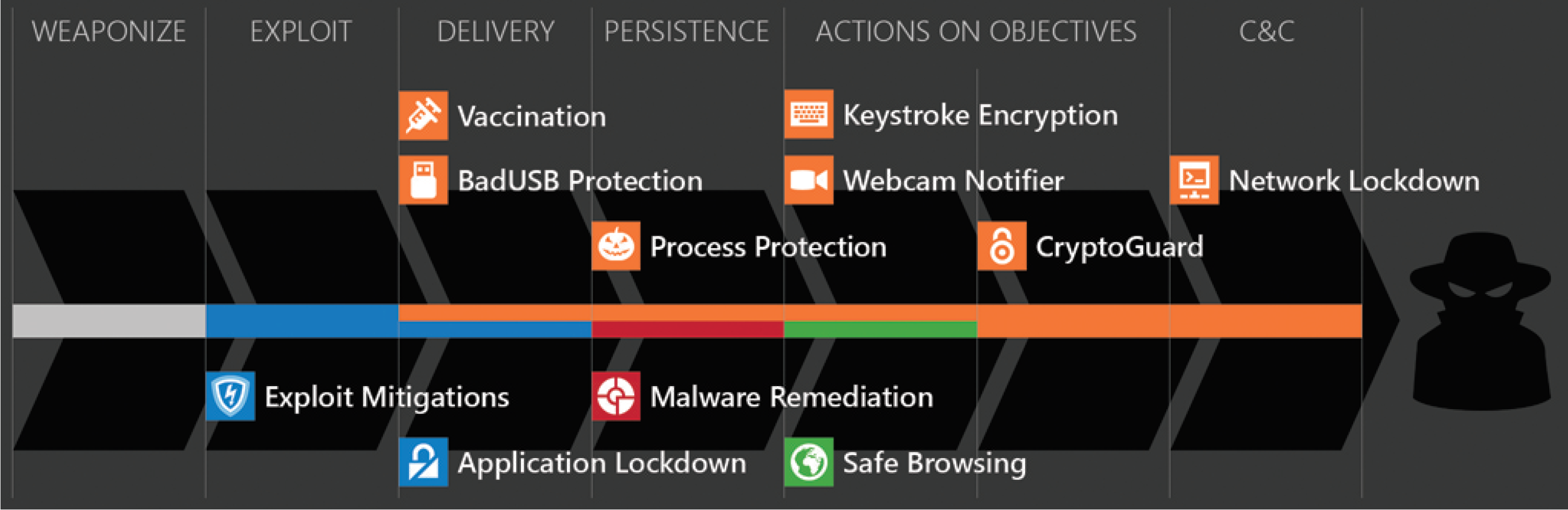 figure 1. Cyber Kill Chain figure 1. Cyber Kill Chain |
At first this 'cyber kill chain ®' might sound aggressive to you. Actually, we are talking about a layered defense strategy here. Within organizations, you might see this tactic applied very often; deploying and relying on multiple individual security technologies 'chained' after each other in an attempt to break down ('kill') the attack and its' related malware artefacts and techniques.
What if we could differentiate these techniques and use this cyber kill chain ® approach on your endpoint? That would be revolutionary wouldn't it? This is exactly what you find in picture x; each part within HitmanPro.Alert works on a particular area. In effect, you have a solution 'killing' exploits and malware on various grounds; they make something emergent that's greater than the sum of the parts!
Within figure 1, you see these various components laid out and explained.
We hope that by now, you are convinced about how special HitmanPro.Alert works. Use this tool alongside your Anti-Virus solution, and you have a solid security foundation.
| *) | HitmanPro utilizes cloud computing and uses advanced heuristic and behavior analysis to reveal even unknown emerging threats. |
| **) | If you are searching a more preventive solution, we suggest you to use HitmanPro.Alert. We do also offer this product for download over here |
| ***) | Only for Windows XP, just a 32-bit (x86) Operating System is supported. |